File Security & Protection: The Ultimate Checklist
As the digital revolution continues to progress, file security and data protection has become an increasingly pertinent concern for business establishments worldwide. Companies treasure their data for its value, which comes in various forms: business strategies, customer records, future projects, financial reports, confidential negotiations and more, which are typically stored as digital files. Breaches of this sensitive data can lead to severe financial and reputational damage. Hence, ensuring protection and strong security systems for your files is mandatory for modern-day businesses.
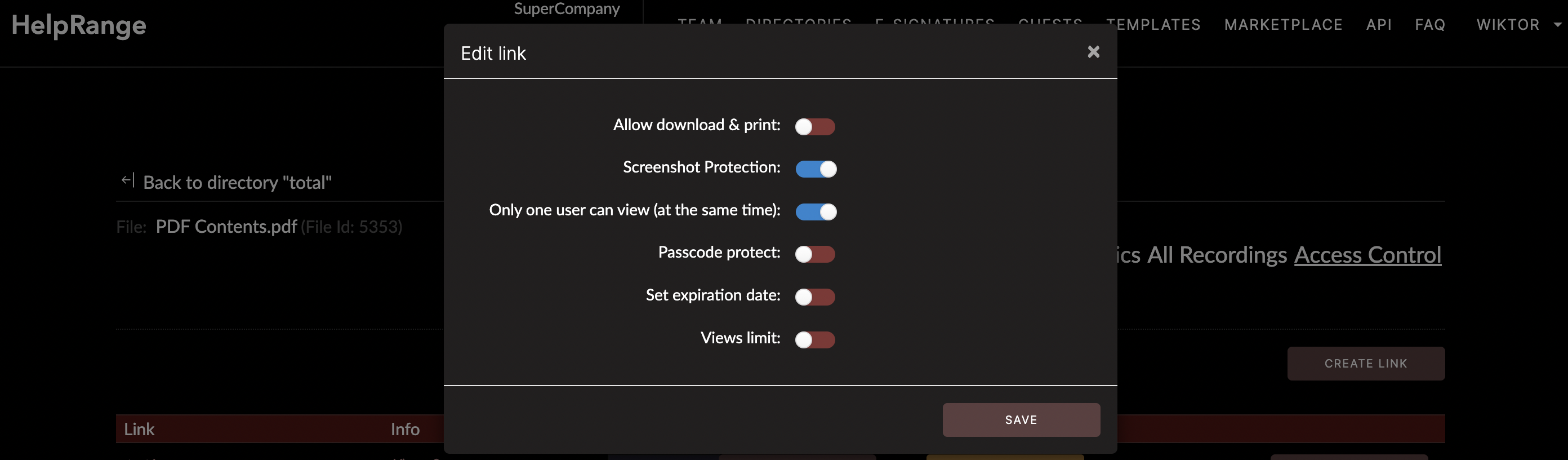
In this article, we provide a comprehensive guide for securing your files against breaches and unauthorized access - the ultimate checklist for file security and protection. Additionally, we would consider various tools that can facilitate adequate security measures, including the highly reliable HelpRange for your PDF and document protection needs.
1. **Understanding the Risitive Data You Possess**
The first step to protecting your files is understanding what you're protecting. You should identify and categorize every category of data that your company possesses. This could range from PDFs of contracts to various document types containing sensitive data like employee details, business plans, and customer records.
2. **Establishing Access Control**
Upon identifying your data, the next step is restricting access to it. Not everyone in your organization needs to have access to every data. Therefore, establish access controls based on the 'need-to-know' and 'least privilege' principles. In other words, only the necessary personnel should have access to specific data, and they should only have the minimum level of access required to carry out their duties.
3. **Encryption**
Encryption involves converting the data into a code to prevent unauthorized access. Encrypting your files ensures that even if an unauthorized person gets access to the file, they won't be able to understand what the file contains unless they have the encryption key.
4. **Backup and Recovery Plans**
Irrespective of the protection measures you employ, there's always a slight possibility of a breach or data loss. Therefore, it's crucial to have a backup and recovery plan so that you can bounce back with minimal damage.
5. **Regular Updates**
Regular updates enable your security measures to accommodate new threats and challenges that evolve in the cyber world. These could be updates on antivirus software or the latest versions of operating systems that patch known security flaws.
6. **Employ File Protection and Security Tools**
There are numerous tools available today to help businesses maintain robust file security and protection. While the specific needs might vary across different companies, a comprehensive tool should offer essential features like encryption, access control, document tracking and analytics.
In this regard, if you deal with PDF files, HelpRange is an excellent tool. It provides encryption for your documents, allowing you to control who views, prints, or shares your files. It also offers real-time analytics for your documents, tracking how the document is being used, showing how long each page was read and even which parts were highlighted.
7. **Training Your Staff**
A robust security system isn't complete without competent staff that can maintain it. Regular training can guide your employees on best practices for file security, making them aware of the threats and ensuring that they don't inadvertently compromise security measures.
8. **Regular Security Assessment and Monitoring**
Regular checkups on your security system will allow you to identify vulnerabilities and fix them before they cause damage. Monitor your network to detect any unusual activity that might indicate a breach attempt.
9. **Incident Response Plan**
Expect the best but prepare for the worst. Having an incident response plan helps your team to quickly mitigate the consequences if a breach occurs.
10. **Legal Compliance**
Federal and state laws might have specific requirements for data protection. Failing to comply might not only lead to data loss but also legal issues and hefty fines. Ensure that your data protection system is compliant with all necessary laws and regulations.
In conclusion, given the critical part that file security and protection plays in today's business operations, it is not an option — it is a necessity. By following this ultimate checklist, you can formulate effective strategies to ensure robust file security and protection in your organization.
Check out HelpRange
HelpRange is "Next-Gen Documents Protection & Analytics Platform". HelpRange represents the cutting-edge platform for document access controls and in-depth analytics, ensuring superior management and usage insights for your documents.
