How to Secure Sensitive Information in Documents
In today's digital age, safeguarding sensitive information has become a top priority for businesses globally. Confidential documents, from strategic plans to client data, play an integral role in every business and must be adequately secured to prevent unauthorized access, loss, and interference. Failure to do so can lead to financial loss, damaged reputation, and potential regulatory implications.
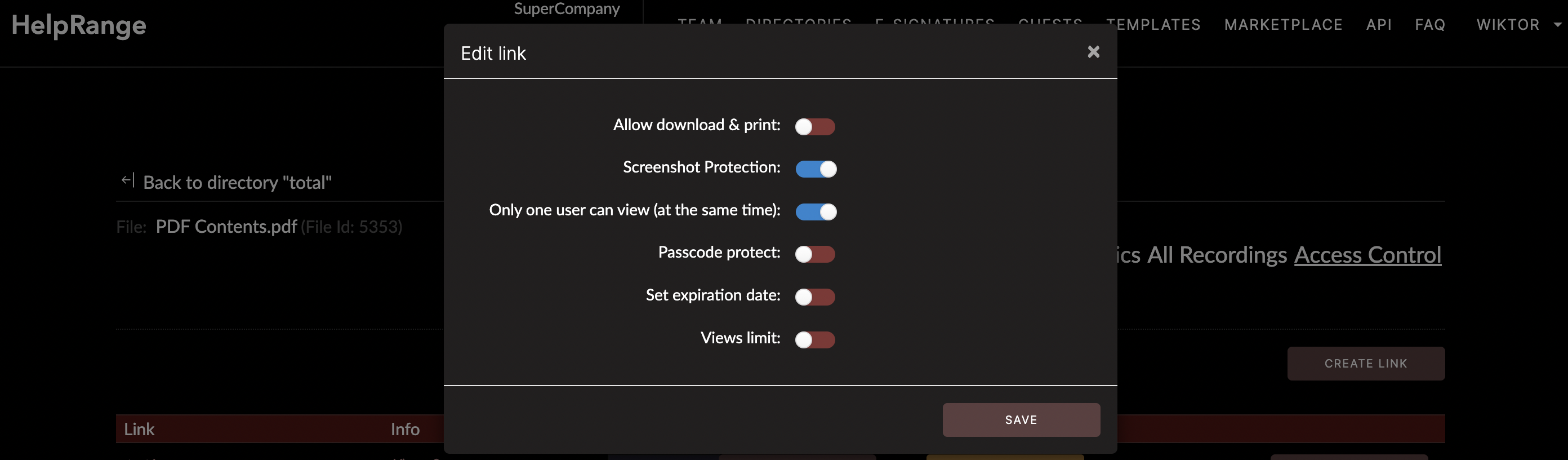
This detailed guide discusses practical methods to secure sensitive information in documents for a more secure working environment. It encompasses various aspects, including specific types of software you can use for document protection and PDF usage analytics, such as HelpRange and others.
1. Establish Robust Access Controls
One of the first lines of defense in securing sensitive information in documents is to implement stringent access controls. Documents containing sensitive information should only be accessible to people who need them to perform their work. Implementing robust access control measures restricts access to these documents, therefore safeguarding against unauthorized access.
2. Employ Strong Passwords
Passwords act as the main gatekeepers to your sensitive documents. It's thus essential to enforce a strict password policy across your organization. For instance, passwords should be long (a minimum of 12 characters), complex (use a combination of letters, numbers, and symbols), and unique (not used for other accounts). Also, passwords should be changed regularly to enhance security.
3. Use Document Encryption
Encryption is a method of converting information into a code that can only be decoded using a special key. It offers a robust method of protecting sensitive information in documents. With modern encryption software, you can encrypt both individual files and entire file systems, ensuring valuable data is only accessible to those with the necessary decryption key.
4. Implement Document Tracking and Management
A document tracking and management system can be a game-changer when managing sensitive information. It can monitor access, changes, deletion, and movement of protected documents. This not only gives you precise control over your files but also provides an invaluable audit trail, offering insights into who accessed the document, when, and what changes were made.
5. Use Document Protection Software
These digital tools offer an extra layer of protection to your documents. Some software options, for instance, allow you to set permissions at a granular level, deciding who can view, edit, print, or copy information from a particular document. Document protection software can also support watermarking to discourage unauthorized sharing and enable document expiration, wherein a document becomes inaccessible after a specific period.
In this realm, you might want to consider HelpRange. It is an online tool that offers PDF and document protection, PDF usage analytics, and PDF tooling. This tool can be incredibly helpful for managing sensitive business documents. It ensures the security of your files while maintaining control of how the documents are used, even after being downloaded or shared.
6. Regular Employee Training
Your employees are either your biggest security asset or your greatest vulnerability. Regularly training your staff on safe computing practices is therefore a vital measure. Remind them on the importance of not sharing sensitive documents or passwords, recognizing potential phishing attempts, and reporting any suspicious activity.
7. Regular Audits and Updates
Regular audits can help identify potential vulnerabilities in your information security system, helping you remediate any discovered weakness. In addition, routinely updating your software, operating systems, and applications is essential to protect against potential security threats.
8. Backup your Documents
Backing up your information is a useful precautionary measure. This way, you have a copy of your sensitive documents in case of any potential data loss. You could opt for secure cloud-based storage solutions or traditional external hard drives, depending on your business needs.
In conclusion, securing sensitive information in documents is a multifaceted endeavor that requires a comprehensive approach. Implementing the methods discussed in this article can significantly bolster your business’s information security and give you peace of mind. Despite the daunting challenges, remember that the cost of a data breach is usually far higher than the cost of investment in robust security measures. Sensitive document security is, therefore, a worthwhile investment for every business.
Check out HelpRange
HelpRange is "Next-Gen Documents Protection & Analytics Platform". HelpRange represents the cutting-edge platform for document access controls and in-depth analytics, ensuring superior management and usage insights for your documents.
