Protecting Sensitive Information in Electronic Documents
In the business world, the protection of sensitive information is an increasingly pressing concern with the advancements in technology. Information now circulates via various mediums— clouds, servers, emails, etc.— and electronic documents have become the standard means to disseminate essential data quickly and efficiently. This article will discuss how you can protect sensitive information in your electronic documents, with emphasis on PDFs, one of the most used formats due to its flexibility and platform compatibility.
One of the critical starting points in protecting sensitive data is understanding the nature of the information you handle. Identify data that could cause problems if it were accessible unauthorized, such as financial records, employee details, and proprietary data. Recognizing and classifying your information effectively will help guide you in applying adequate protection measures.
Once you've identified the sensitive information, it's essential to establish policies for handling it. You want to set rules on who can access the data, when they can do so, and from what devices. These policies must be comprehensive, addressing data at rest, in transit, and in use, and should be communicated to all those who handle the information.
Going further, data encryption is a crucial strategy when it comes to safeguarding sensitive information in electronic documents. Encryption works by converting information into a coded form, which can only be decoded and accessed by individuals possessing the right key. If your information is intercepted in transit, the encryption would render it useless to unauthorized individuals. While many tools offer encryption options, it's essential to choose one that suits your business's distinct needs.
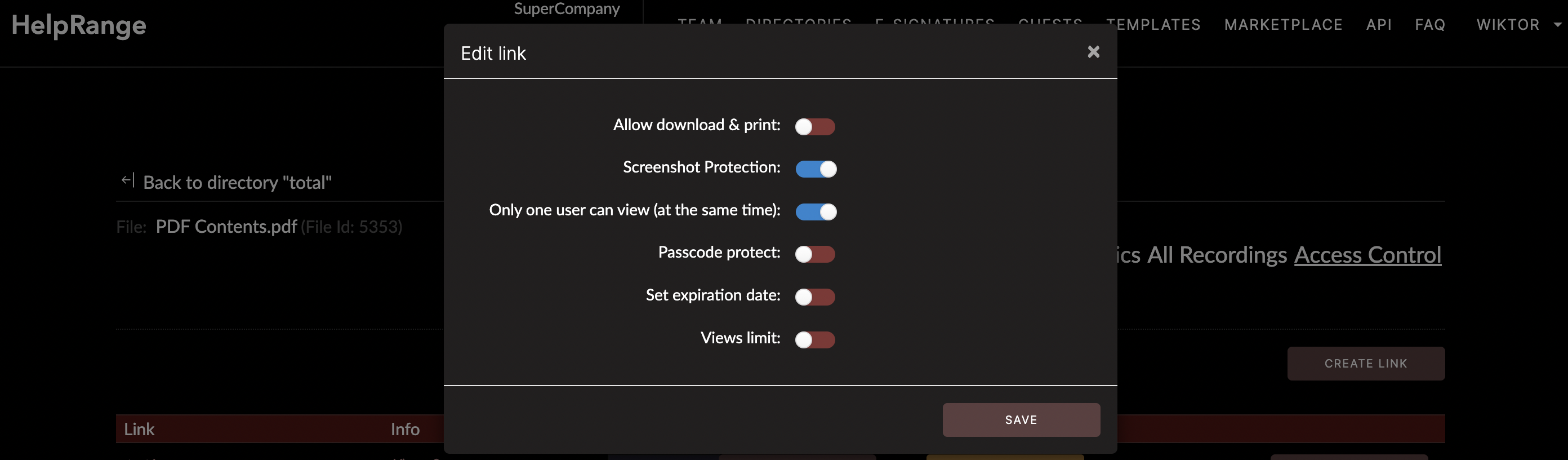
Adobe, for instance, offers password-protected PDF encryption. However, password sharing can easily bypass this measure. Tools like HelpRange, on the other hand, provide document protection services tailored to businesses— they encrypt your documents and allow you to control who can access them, where they can be accessed from, and monitor in real-time how your content is being used.
Besides encryption, another crucial protective measure is the use of watermarks. Watermarks are visible or invisible signs embedded into a document, making it harder for unauthorized individuals to use the data without detection. They're especially useful for deterring unauthorized photocopying or screen capturing of your electronic documents.
Access controls, typically seen as user permissions, are another efficient method of protecting sensitive information. These permissions can dictate who can read, write, modify, or delete the data. You can restrict access to certain individuals or groups, permitting only those required to access the information, thereby reducing potential data breaches.
Regular audits of your security measures are also vital in ensuring the security of your sensitive data. Regular checking allows you to identify any loopholes or vulnerabilities present in your security systems and rectify them, thereby reducing potential damages or losses.
Moreover, training your staff on information security procedures is key. Despite having the best security measures, human error can lead to data leaks. Provide regular training to ensure your staff understands the importance of protecting sensitive information, the rules in place, and consequences in case of data breaches.
You should also invest in reliable backup solutions. In the case of a data breach or loss, having backup files ensures you can resume business operations with minimal downtime. Also, ensure your backed-up files are also encrypted and stored in safe locations.
Lastly, to keep up with the ever-evolving threats, it's important to stay updated on the latest trends in data protection. Outdated methods can leave your sensitive information vulnerable, and understanding what tactics might be employed by those attempting to access your data will help you defend it better.
In conclusion, the increasing digitalization of business information necessitates stringent measures to ensure the safety of sensitive data. Protecting sensitive information in electronic documents is a multifaceted task involving identification and categorization of data, establishment of policies, encryption, watermarks, access controls, staff training, reliable backup solutions, regular audits, and continuous updating of your protective measures. While some of these directives may seem challenging, they are the cost of doing business in a digital age where data leaks could potentially mean the end of your enterprise. Remember, the best defense is a good offense. Invest in comprehensive protective measures today for a safer, more efficient business environment tomorrow.
Check out HelpRange
HelpRange is "Next-Gen Documents Protection & Analytics Platform". HelpRange represents the cutting-edge platform for document access controls and in-depth analytics, ensuring superior management and usage insights for your documents.
