The Different Types Of File Security Protection
In today's digital age, file security has taken a center stage in the realm of data protection. Enterprises, whether small or large, depend heavily on data, making it a treasured resource. Thus, it is crucial to implement robust security measures to safeguard files and documents from unauthorized access, corruption, or hacking. Understanding the different types of file security protection is therefore an indispensable undertaking for both businesses and individuals.
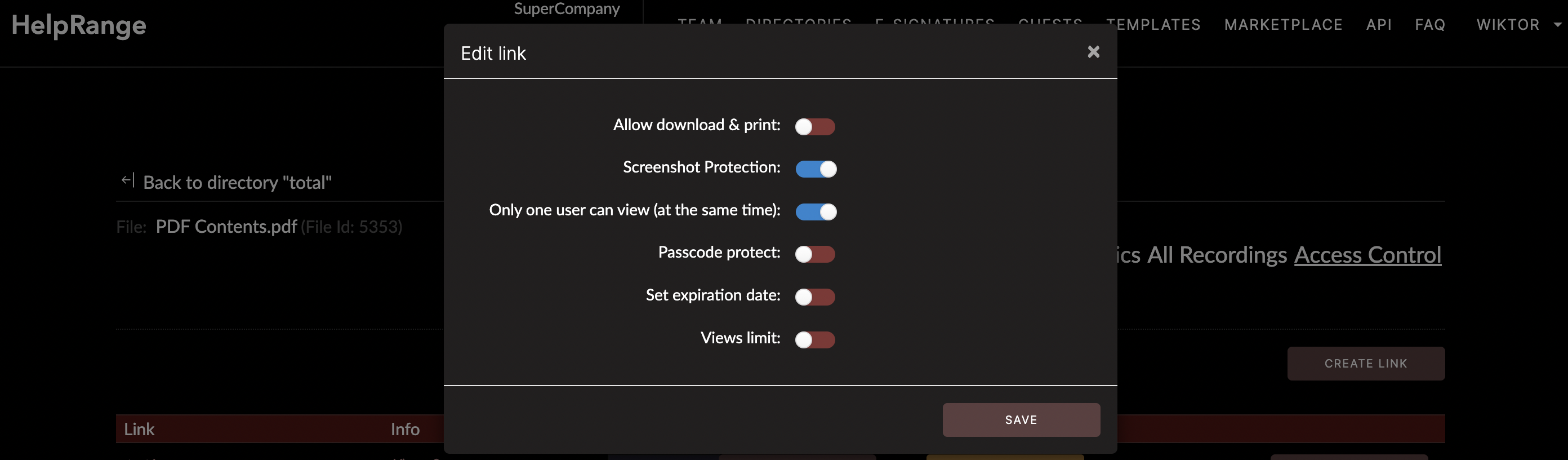
File security protection allows for access control, data encryption, backup solutions, and user-level permissions. Here, we will delve into the various types, including access control, data encryption, backup solutions, digital rights management, and password protection. Additionally, we will highlight how services like our own - HelpRange, can assist in securing your files and documents.
**Access Control**
At the heart of file security lies controlling who can access what. Access control measures help manage users' permissions to view, change, download, or share files and documents. They provide a way to centrally control access rights, specifying the level of involvement each user or user group can have with the shared documents. It helps deter unauthorized access and prevent sensitive information from falling into the wrong hands.
Some systems come with in-built access control like Microsoft's NTFS file system, where the owner can set permissions for files or folders. Additionally, cloud-based file storage providers like Dropbox, Google Drive, and OneDrive offer extensive access control settings.
**Data Encryption**
Data encryption, another vital aspect of file security protection, uses algorithms to change readable text into unreadable characters, protecting the file from unauthorized access. Even if the data falls into the wrong hands, it remains meaningless without decryption.
Various tools offer data encryption services, from Microsoft's BitLocker, which can encrypt entire drives, to individual file encryption tools like Axcrypt. These tools use a set of keys for encryption and decryption, providing a robust level of security for your documents.
**Backup Solutions**
Backup solutions are vital in ensuring data redundancy and resilience. They help protect files and documents from accidental deletion, hardware failures, or even malicious attacks like ransomware.
Cloud-based backup services like Google Backup and Sync, or hard-drive based solutions like Windows Backup and Restore, provide easy ways to automate regular backups. More comprehensive solutions like Acronis True Image not only backup your data but also come with inbuilt ransomware protection.
**Digital Rights Management (DRM)**
DRM controls what a user can do with a document after gaining access. They limit actions such as copying, printing, or sharing, adding another layer of protection even after access control measures are passed.
DRM tools, mainly used for multimedia files, can also protect PDFs and other documents. For instance, Adobe's Digital Edition offers DRM protection for PDFs and ePub files.
**Password Protection**
**Public Key Infrastructure (PKI)**
Finally, Public Key Infrastructure (PKI) security method uses a pair of keys – a public and a private key – for encryption and decryption. The recipient’s public key encrypts the data, and the corresponding private key decrypts it. PKI provides secure authentication and data encryption and ensures data integrity and non-repudiation.
In conclusion, different types of file security protections serve different purposes but all work to ensure your data remains safe in its stored, in transit, and in use states. Leveraging these data security measures, each serving a unique purpose, will provide a comprehensive data protection strategy. An indicated, platform like HelpRange can serve a vital role in some facets of this strategy. However, it's crucial to remember that attacks continually evolve, and so must your protections. Always stay aware and informed of new threats and solutions to maintain effective file security. Be vigilant, proactive, and unfold an array of security measures to protect sensitive data from prying eyes.
Check out HelpRange
HelpRange is "Next-Gen Data Room For Documents Protection & Analytics". HelpRange is a cutting-edge virtual data room platform for document access controls and in-depth analytics, ensuring superior management and usage insights for your documents.
